This blog post details the options for doing client authentication before/after LWA handshake in the Online Offer Construct and the Amazon recommended approach.
1. Client authentication after LWA handshake [Recommended]
The customer is asked to perform client authentication after LWA consent page shows up. Client needs to generate the token-pair from the authorization code and keep it temporarily associated to the customer’s session. Once customer performs authentication, client can update the association to reflect the relationship of customer to the token-pair.
Pictorial Diagram
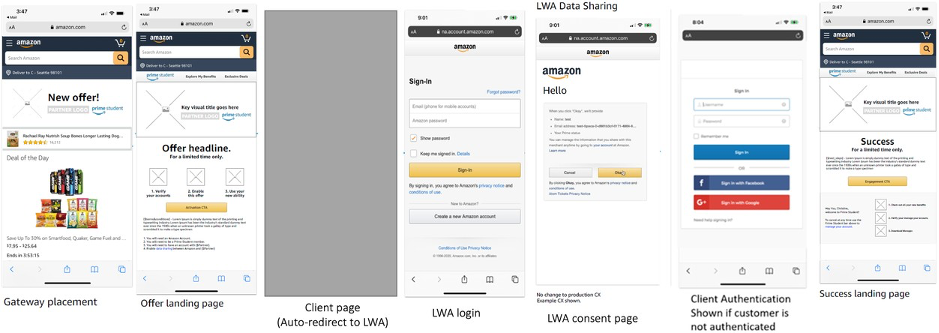
Why it’s recommended?
This approach is focused at giving customers a better CX while taking them from Amazon to the client website.
- Initiating LWA consent flow at the client side right after customer’s interaction on Amazon retail website seems to be a smooth transition while taking customer from Amazon domain to the client domain. Once LWA flow completes, customer expects to be interacting with the client domain.
- Since client invokes the LWA consent flow before asking customers to log-in and provide their details at their end, customer is informed very well in advance about the data-sharing policies between Amazon and the client.
Prerequisites
There are certain prerequisites to follow this approach, which are listed in the LWA Integration guide here.
2. Client authentication before LWA handshake
The customer is asked to perform client authentication before LWA consent page shows up. Since authorization code has an expiry of 5 minutes and if customer takes longer than that to perform authentication/login at the client end, then client needs to initiate LWA handshake again to get a new authorization code and exchange it for the token-pair (access token and refresh token).
If LWA handshake is supposed to happen before client authentication, then client needs to generate the token-pair and keep it temporarily associated to the customer’s session till customer logs in.
If customer is already logged in at client’s end, then it doesn’t really make a difference since customer is not asked to perform authentication by client.
Pictorial Diagram
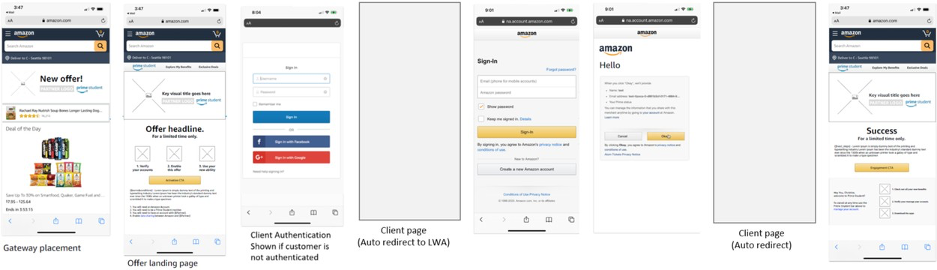
Why it’s not recommended?
We feel the CX in this approach is not as good as compared to the previous approach for following reasons:
- When a customer is taken from Amazon website/app to the client website/app, one expects that the interaction with Amazon is over and now completely moved to the client domain. However, if customer is not logged-in already at the client side, then customer is asked to perform the authentication at the client end before being asked for consent on the LWA screen.
- The CX may appear confusing to the customer. However, with proper messaging at the client login screen or the wait screen before LWA handshake is initiated, customer can be informed about what to expect next in the flow.
This approach should be considered in those cases when:
- Client does not own a data store to associate the customer’s session to the token-pair generated after LWA handshake.
- It is too much of an overhead for the clients to create and maintain this data store.